Sonatype Container
24/7 Container Protection You Can Trust
Rest assured, knowing your containers and Kubernetes deployments are secured consistently as they move from build to production on multiple cloud platforms. We’ve got you covered with around-the-clock protection.
ENTERPRISE SECURITY
Identify
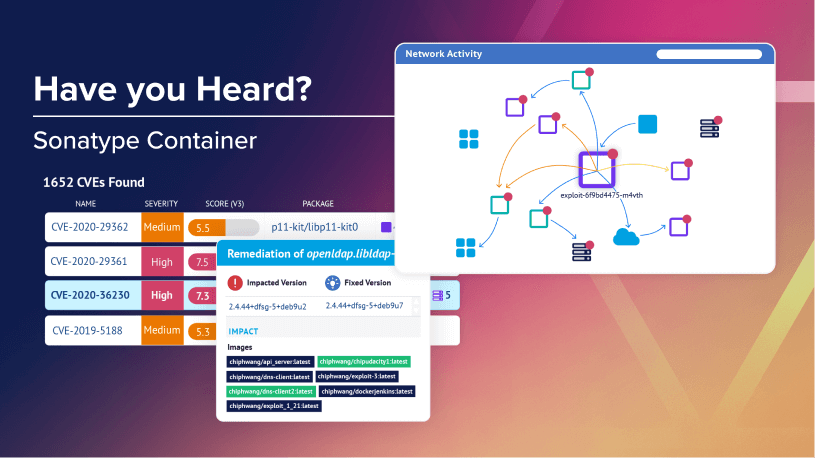
Know any vulnerabilities or compliance issues before containers even deploy.
Prevent
Avoid cyber attacks with real-time visibility into network activity in production.
Enforce
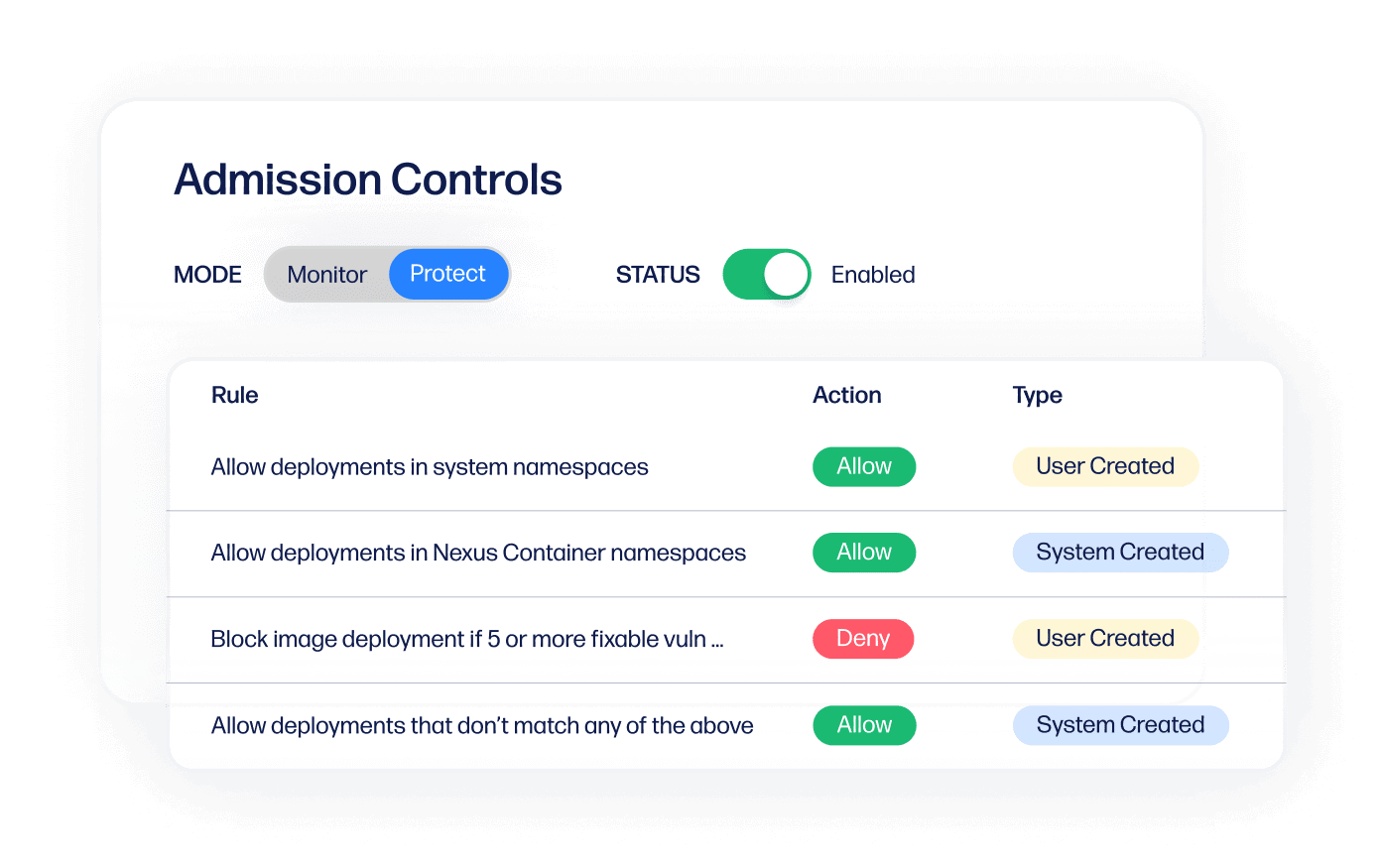
Save time on policy management with behavioral learning that enforces policies for you.
Automate
Enable end-to-end container security throughout the entire CI/CD pipeline and at run-time.
Identify threats in development
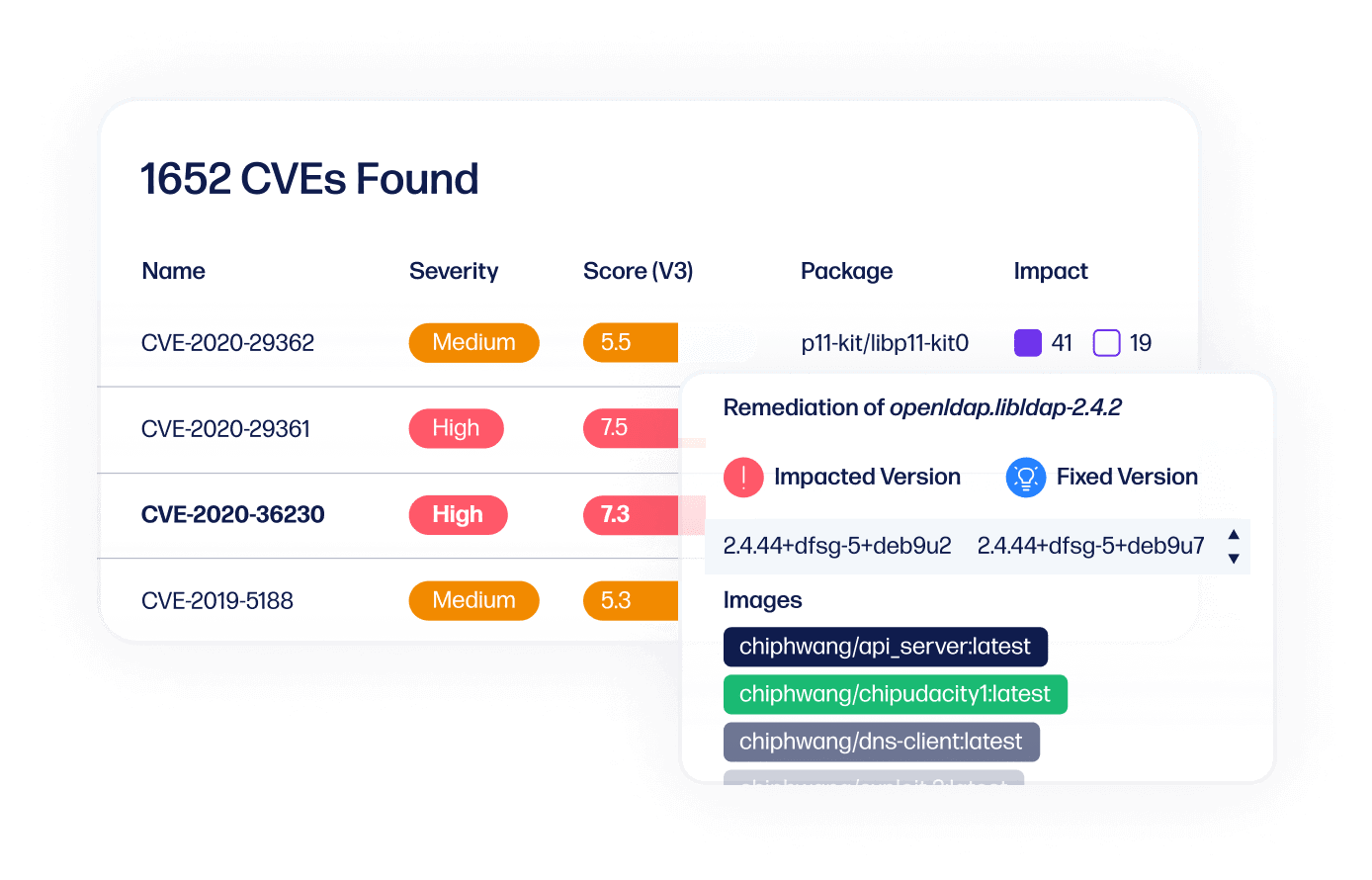
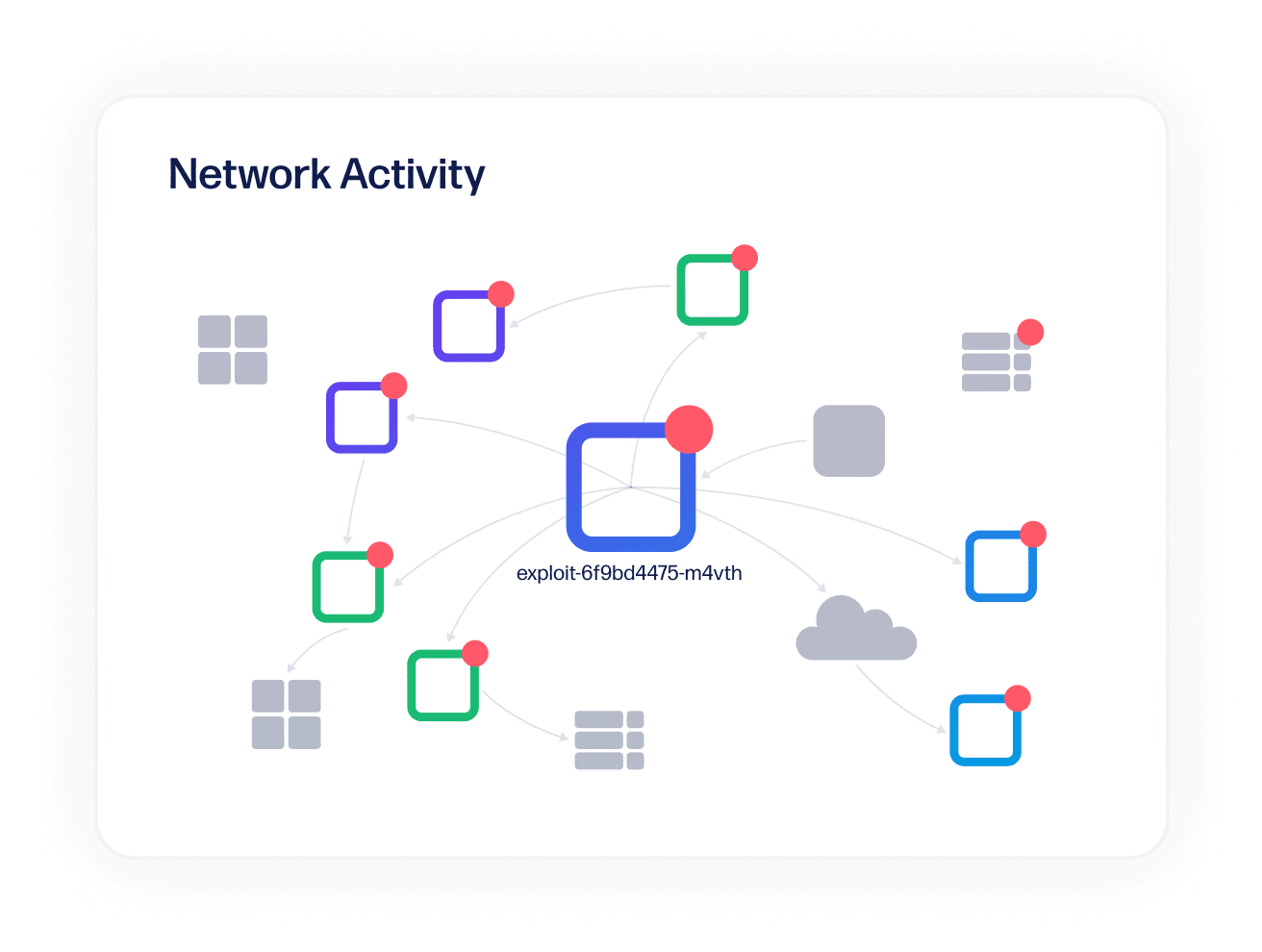
Protect running containers
Enforce policies automatically
Work with the tools you already use
Orchestration & management platforms

Kubernetes

Red Hat OpenShift (certified container & operator)
Rancher (catalog listed)

Amazon ECS

Amazon EKS

Apache Mesos

Google Cloud Platform (GCP)

Google Kubernetes Engine (GKE)

Azure Kubernetes Service (AKS)
IBM Cloud

Oracle Kubernetes Engine (OKE)

Pivotal Container Service (PKS)

Diamanti

VMWare Tanzu
Explore the Sonatype platform.
Intercept malicious open source at the door.
Reduce risk across software development.